Detect and examine TLS packets. More...
Classes | |
| struct | ClientHello |
Enumerations | |
| enum | ContentType { ContentType::Change_cipher_spec = 20, ContentType::Alert = 21, ContentType::Handshake = 22, ContentType::Application_data = 23 } |
| enum | HandshakeType { HandshakeType::Hello_request = 0, HandshakeType::Client_hello = 1, HandshakeType::Server_hello = 2, HandshakeType::Certificate = 11, HandshakeType::Server_key_exchange = 12, HandshakeType::Certificate_request = 13, HandshakeType::Server_hello_done = 14, HandshakeType::Certificate_verify = 15, HandshakeType::Client_key_exchange = 16, HandshakeType::Finished = 20 } |
Functions | |
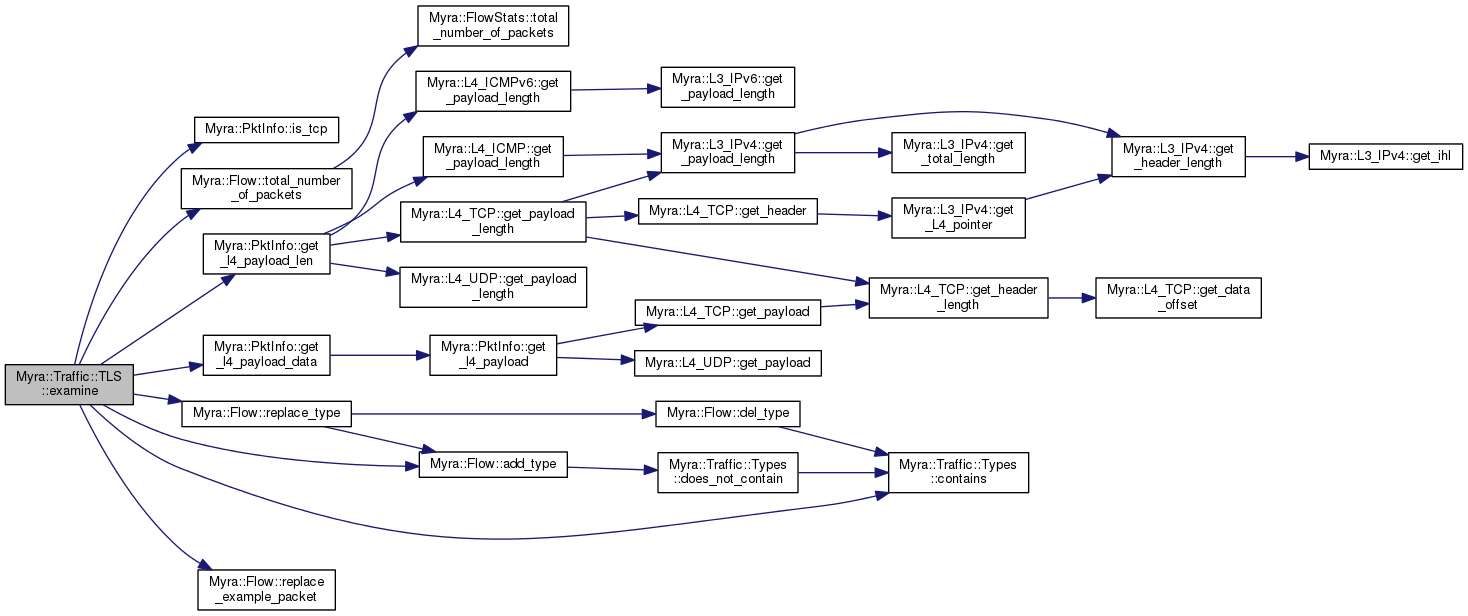
| bool | examine (Flow &flow, const Myra::PktInfo &info) |
| Examine a packet for TLS, and mark the flow if found. More... | |
Detect and examine TLS packets.
|
strong |
|
strong |
| bool Myra::Traffic::TLS::examine | ( | Myra::Flow & | flow, |
| const Myra::PktInfo & | info | ||
| ) |
Examine a packet for TLS, and mark the flow if found.
true if this exam needs to be called again for the given flow false if this exam never needs to be called again TLS "client hello" handshake packets start like this:
-> flow #4853955849062914786: Unknown+FlowStart+IP+IPv4+TCP: 10.0.1.11:57530->31.13.70.1:443 (data len: 195, number of packets: 4)
-> flow #4853955849062914786: payload: number of bytes: 195
0: 16 03 01 00 be 01 00 00 ba 03 03 54 da 2d 99 8b 40 3a 9f 0d f9 1e e8 34 06 fd 95 2f 4b 5e 63 0e - ...........T.-...:.....4.../K^c.
20: d3 71 99 9d 61 ee 9f 8c d9 4d e1 00 00 38 cc 14 cc 13 cc 15 c0 14 c0 0a 00 39 00 38 00 35 c0 12 - .q..a....M...8...........9.8.5..
40: c0 08 00 16 00 13 00 0a c0 2f c0 2b c0 13 c0 09 00 a2 00 9e 00 33 00 32 00 9c 00 2f c0 11 c0 07 - ........./.+.........3.2.../....
60: 00 05 00 04 00 ff 01 00 00 59 00 00 00 15 00 13 00 00 10 77 77 77 2e 66 61 63 65 62 6f 6f 6b 2e - .........Y.........www.facebook.
80: 63 6f 6d 00 23 00 00 00 0d 00 22 00 20 06 01 06 02 06 03 05 01 05 02 05 03 04 01 04 02 04 03 03 - com.#.....". ...................
Note the first few bytes:
Value | Meaning -------------------——+--—— 0x16 | handshake (22 decimal) 0x03 | major version 0x01 | minor version 0x00 0xbe | length 0x01 | client hello 0x00 0x00 0xba | length 0x03 | client major version 0x03 | client minor version
If the packet is TLS client hello, also check to see if we have a SNI (server name indication) extension.
SNI looks like this:
60: 00 05 00 04 00 ff 01 00 00 59 00 00 00 15 00 13 00 00 10 77 77 77 2e 66 61 63 65 62 6f 6f 6b 2e - .........Y.........www.facebook.
80: 63 6f 6d 00 23 00 00 00 0d 00 22 00 20 06 01 06 02 06 03 05 01 05 02 05 03 04 01 04 02 04 03 03 - com.#.....". ...................
Value | Meaning --------------------------—+-----— 0x00 0x00 | server name extension (RFC 4366 section 2.3) 0x00 0x15 | extension length 0x00 0x13 | list length 0x00 | name type (must be zero for "hostname") 0x00 0x10 | name length www.facebook.com | host name